Some users receive legitimate voicemail to email communication, but the real emails containing legit Baylor voicemails will not contain any links. Any email like the one below that requires you to click a link (a hidden link at that) & authenticate should be viewed with skepticism (especially one with poor grammar & odd wording).
Category Archives: Phishing
Office 365 Business Essentials Bill Is Ready
In this phishing email the scammers are hoping you click on the link to pay the invoice, but in reality you will just be giving away your credentials instead. As Baylor Faculty, Staff, & Students, you do not have any Office 365 bills to pay. Also, if you notice the sending address has nothing to do with Microsoft or Office & the link goes to a site that lacks Microsoft or Office in the URL. You can safely ignore & delete this phishing email from your inbox.
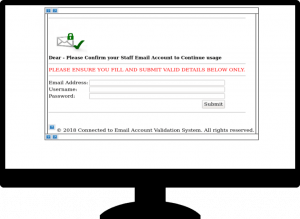
Quarterly Pay Information
Baylor does not communicate payroll changes in this format – the email address is not a Baylor address, the link does not go to a Baylor site. The other telltale signs of a phish are the generic greeting, the poor spacing, & the generic closing. If you receive an email that looks anything like this one, please ignore it by not clicking the link & delete the email from your inbox.
Phishing from the University at Buffalo?!?!?
Earlier today over a thousand users received an email saying that due to repeated “shot down emails sent to our internal server” that your email would be deactivated until you clicked a button that would “Login to Restore Account”. The phishers must have confused UB (University at Buffalo) for BU (Baylor University). This email did not originate from Baylor & was a phishing attempt that can be ignored & deleted. I hope this one was obvious to Baylor email users, as always please forward any suspicious emails to abuse at Baylor dot edu.
Sharepoint/One Note
A fake Microsoft OneNote/SharePoint email has been spotted on campus recently, this one did not have the pictures come through correctly, but the one you see may have graphics to lend more credibility to the phishing message. These messages may look real, but if you have not used SharePoint or OneNote by logging & uploading document(s) then the best course of action is to either ignore & delete the phish and/or to log in to the real SharePoint or OneNote site to see if any documents are uploaded on the actual site.
Action Center Alert!
You get an email with a scary sounding subject line informing you that your email account has security flaws & the baylor.edu admin team needs you to kindly click a link to update your account or ALL YOUR EMAIL WILL BE HELD! This type of phish is designed to make you panic, from its official sounding sending address (support@baylor.edu) to the group that supposedly sent the message (baylor.edu admin team) to the threat of stopping all new mail from arriving in your inbox. Usually when an email provides a significant threat & gives you very little time to complete the action, it is not a legitimate email.
Yes, Phishing is Still Happening…
So you requested your email account to be deactivated & are now receiving a notice to let you undo that request…wait, what?!?! Current students, faculty, and/or staff may sometimes wish they could deactivate their email (to avoid all the phishes & spam, of course), but there is not a process that allows you to request deactivation & then click a button or link to undo that deactivation request. If you look at the email below, you will also notice that it came from an outside/non-Baylor email address, which should raise some red flags & the screenshot of where the link takes you looks nothing like any Baylor web page you have ever seen. Just another example of phishing, but this one is (hopefully) easy for you to catch & delete!
Screenshot Of Website that loads when you click the phishing link:
Mail Synchronization Phish
Ah yes, the old click here to synchronize your email or you won’t be able to send or receive email & it is mandatory…wait, what?!?! This message may look legit, but this is not something that Baylor ITS will ask you to do. Please observe the philosophy of ‘when in doubt, throw it out’ & delete this message if you receive it.
Phishing Continues…
We are still seeing high numbers of the message unavailable emails with a familiar to you subject line & many users are still clicking the links & giving away their passwords. Please encourage everyone to be careful when clicking links & do not enter your Baylor credentials on any site that you access directly from a link in your email.
This morning we received the following phishing email from a user. It appears to come from Microsoft & warns that you have had abnormal behavior on your email account & if you don’t click the ‘Confirm’ button that you will not receive any new mail. This is a common tactic, designed to get you to panic & without thinking click the link & enter your Baylor account & password. It even says that you should log in with you email & password to confirm & to be sure to do so in a safe & secure manner – this statement is designed to lend legitimacy to the email & to make you relax your guard because the email must be real if it is offering security advice. Also note that it is signed BaylorCorporation…we are not a corporation & even if we were it would likely be 2 separate words.
Let’s all do our part to Sic Phishing on campus to keep our email accounts & our personal information as secure as possible!
Duo Now Protects Your Email & More!
So now that we have rolled out Duo to Office 365 & our Baylor email a bit quicker than anticipated, does that mean we can all relax & forget about phishing emails?
In short, no.
The longer answer is because phishing emails will never completely disappear since they are a cheap & easy way to attempt to obtain credentials from authorized users of a system. Plus, there is always the potential that the phisher could get a user to slip up & not only type in their username & password, but then accept the Duo authentication method that they choose to send out. Please keep forwarding any phishing messages you receive to BearAware at Baylor dot edu & do NOT accept any Duo pushes, send passcodes to unknown persons, or push a button to authorize a phone authentication when you were not the one initiating the Duo authentication. Duo is an excellent step to protect our environment, but we still need everyone’s help to keep Baylor & your information cyber-secure.