A fake Microsoft OneNote/SharePoint email has been spotted on campus recently, this one did not have the pictures come through correctly, but the one you see may have graphics to lend more credibility to the phishing message. These messages may look real, but if you have not used SharePoint or OneNote by logging & uploading document(s) then the best course of action is to either ignore & delete the phish and/or to log in to the real SharePoint or OneNote site to see if any documents are uploaded on the actual site.
Author Archives: Will
Action Center Alert!
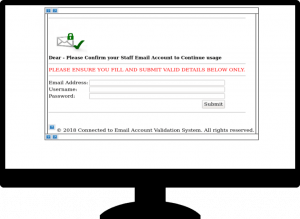
You get an email with a scary sounding subject line informing you that your email account has security flaws & the baylor.edu admin team needs you to kindly click a link to update your account or ALL YOUR EMAIL WILL BE HELD! This type of phish is designed to make you panic, from its official sounding sending address (support@baylor.edu) to the group that supposedly sent the message (baylor.edu admin team) to the threat of stopping all new mail from arriving in your inbox. Usually when an email provides a significant threat & gives you very little time to complete the action, it is not a legitimate email.
Latest News
Instead of the click here to re-activate your mailbox from being permanently deleted or green boxes inviting us to view the entire message, we are seeing a bunch of the previously mentioned extortion scam emails & the ones that come from outside of Baylor but are pretending to be from leadership (your supervisor, deans, the athletic director, head coach, or even President Livingstone) inviting you to respond to an urgent request that cannot be handled on the phone because the sender is in a meeting that they cannot step away from. Although these may not be your traditional phishing emails, they are still scam emails & we wanted to highlight both of them here again. One thing you will notice, especially in the adult content extortion email – the spelling, punctuation, & grammar are odd. This is usually a sign that the email is being run through some sort of language translator & a big indicator that the email is a scam.
Adult Website Extortion Scam (this one is quite lengthy & uses some interesting spacing & line breaks…)
Fake Request From Leadership Emails (notice the @my.com email address, they have also used Gmail addresses in the past)
Yes, Phishing is Still Happening…
So you requested your email account to be deactivated & are now receiving a notice to let you undo that request…wait, what?!?! Current students, faculty, and/or staff may sometimes wish they could deactivate their email (to avoid all the phishes & spam, of course), but there is not a process that allows you to request deactivation & then click a button or link to undo that deactivation request. If you look at the email below, you will also notice that it came from an outside/non-Baylor email address, which should raise some red flags & the screenshot of where the link takes you looks nothing like any Baylor web page you have ever seen. Just another example of phishing, but this one is (hopefully) easy for you to catch & delete!
Screenshot Of Website that loads when you click the phishing link:
Mail Synchronization Phish
Ah yes, the old click here to synchronize your email or you won’t be able to send or receive email & it is mandatory…wait, what?!?! This message may look legit, but this is not something that Baylor ITS will ask you to do. Please observe the philosophy of ‘when in doubt, throw it out’ & delete this message if you receive it.
Phishing Continues…
We are still seeing high numbers of the message unavailable emails with a familiar to you subject line & many users are still clicking the links & giving away their passwords. Please encourage everyone to be careful when clicking links & do not enter your Baylor credentials on any site that you access directly from a link in your email.
This morning we received the following phishing email from a user. It appears to come from Microsoft & warns that you have had abnormal behavior on your email account & if you don’t click the ‘Confirm’ button that you will not receive any new mail. This is a common tactic, designed to get you to panic & without thinking click the link & enter your Baylor account & password. It even says that you should log in with you email & password to confirm & to be sure to do so in a safe & secure manner – this statement is designed to lend legitimacy to the email & to make you relax your guard because the email must be real if it is offering security advice. Also note that it is signed BaylorCorporation…we are not a corporation & even if we were it would likely be 2 separate words.
Let’s all do our part to Sic Phishing on campus to keep our email accounts & our personal information as secure as possible!
Duo Now Protects Your Email & More!
So now that we have rolled out Duo to Office 365 & our Baylor email a bit quicker than anticipated, does that mean we can all relax & forget about phishing emails?
In short, no.
The longer answer is because phishing emails will never completely disappear since they are a cheap & easy way to attempt to obtain credentials from authorized users of a system. Plus, there is always the potential that the phisher could get a user to slip up & not only type in their username & password, but then accept the Duo authentication method that they choose to send out. Please keep forwarding any phishing messages you receive to BearAware at Baylor dot edu & do NOT accept any Duo pushes, send passcodes to unknown persons, or push a button to authorize a phone authentication when you were not the one initiating the Duo authentication. Duo is an excellent step to protect our environment, but we still need everyone’s help to keep Baylor & your information cyber-secure.
Subject Line Woes…
Today we saw another phishing message that borrowed a familiar subject line from the email inbox of the person sending the phishing messages…this time they used our BearAware Alert: Active Phishing Event subject line from last week. Please ignore & delete this message if you see it & always be skeptical of emails that look like the examples below this post.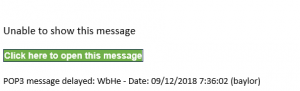

Phishing Alert – Click here…
Baylor communications will contain information in the email message & may include instructions on how to access more information online (or web addresses), but they avoid just having a ‘Click here to open this message’ link with no other information. This phishing scheme lends legitimacy to the message by re-using a subject line that the recipient has seen before, probably very recently. It also uses the interlocking BU logo on the page where it asks you to log in while prompting you with your full Baylor email address (yet another trick they use to lend legitimacy to the message).
Remember you can forward any suspected phishing email to BearAware at Baylor dot edu. As always, Sic Phishing!
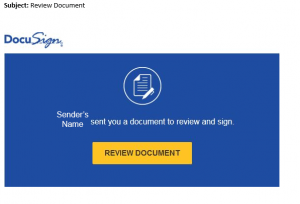
Phishing Alert – DocuSign Review Document
As a slight twist on phishing emails we have been seeing for the past couple of weeks, one rolled in this morning with the DocuSign logo at the top. However, this is not from DocuSign & does not contain a document for you to review & sign. If you clicked the link, please change your BearID password immediately. Remember, you can forward any suspected phishing email to BearAware at Baylor dot edu. #SicPhishing